How to Design a Scalable and Secure API Architecture: A Comprehensive Guide
Posted by: Deepak | April 24, 2024
Categories: Secure API Design, API Best Practices, API Security
In today's digital landscape, APIs (Application Programming Interfaces) have become the cornerstone of interconnected applications and services. As the volume and complexity of API interactions increase, designing a scalable and secure API architecture becomes paramount. This blog delves into the essential principles and best practices for crafting robust API architectures, exploring the technical considerations, industry use cases, and the latest tools available. By following this comprehensive guide, you can empower your APIs to handle growing demands while maintaining robust security protections.
Core Principles of Scalable and Secure API Architecture
A well-designed API architecture hinges on several key principles:
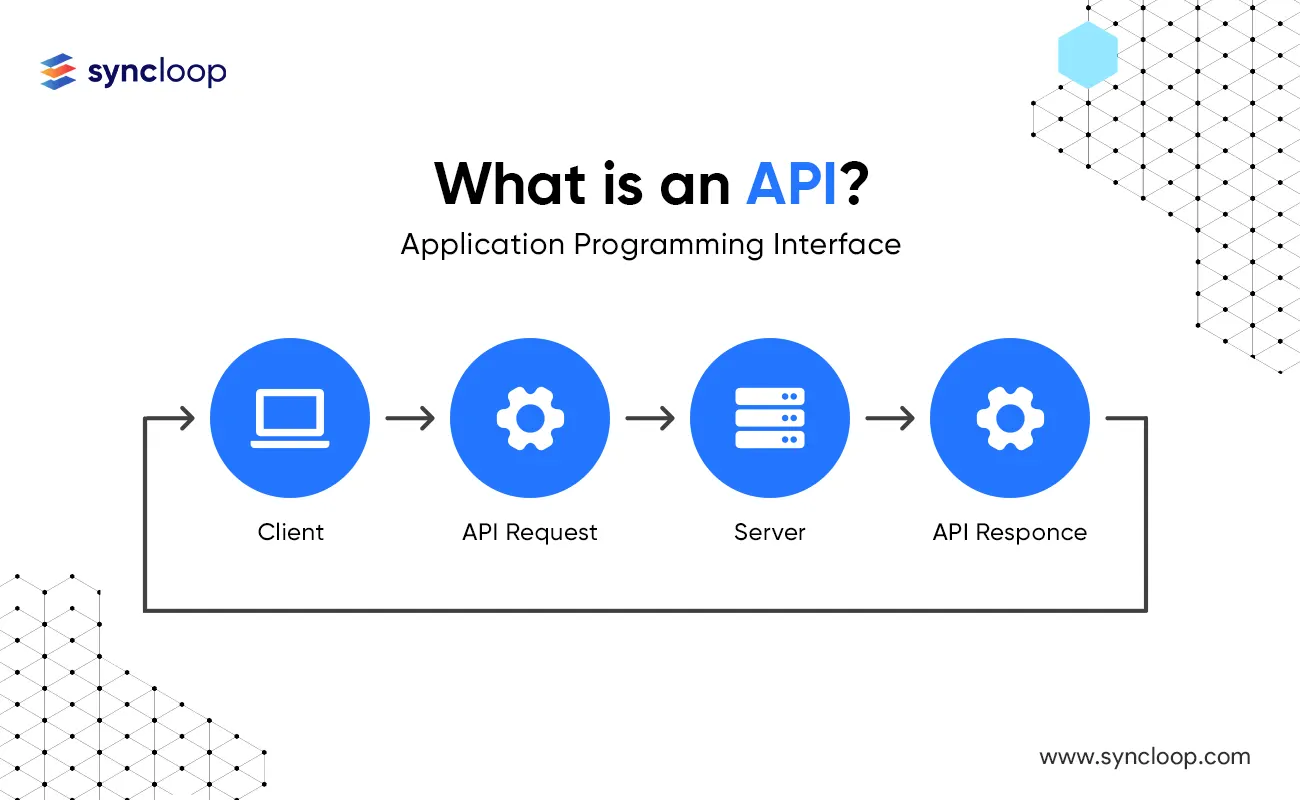
- Stateless Design: Each API request should contain all necessary information for processing, eliminating the need for server-side session management. This simplifies scaling and improves performance.
- Resource-Oriented Design: Model APIs around resources (e.g., users, products), providing clear endpoints for accessing, creating, updating, and deleting those resources.
- API Versioning: Implement a well-defined versioning strategy to manage API evolution, allowing for introducing new features and deprecating older versions gracefully. (Discussed in detail in a previous blog post about API Versioning).
- Security Best Practices: Enforce robust security measures like authentication, authorization, encryption, and input validation to safeguard sensitive data and prevent unauthorized access.
- Monitoring and Logging: Implement comprehensive monitoring and logging practices to track API usage, identify potential issues, and ensure smooth operation.
Statistics show the growing importance of scalability and security. According to a 2023 report by Apigee, 82% of developers consider scalability a critical factor in API design, highlighting the need for architectures that can handle increasing traffic volumes.
Best Practices for Building Scalable and Secure APIs
Here are some key practices to translate these principles into a robust API architecture:
- Microservices Architecture: Break down your API into smaller, independent microservices that can be scaled independently based on their needs.
- Load Balancing: Distribute incoming API requests across multiple servers to ensure efficient resource utilization and prevent bottlenecks.
- Caching: Implement caching mechanisms to store frequently accessed data, reducing server load and improving response times.
- API Rate Limiting: Enforce rate limits to prevent abuse and ensure fair access to API resources.
- API Gateway: Utilize an API gateway as a single entry point for managing API traffic, enforcing security policies, and offloading tasks like authentication from backend services.
Industry Use Cases: Scalability and Security in Action
Scalable and secure API architectures are essential across various industries:
- E-commerce: E-commerce platforms require APIs that can handle high traffic spikes during peak shopping seasons. Scalable architectures ensure smooth user experience even under heavy load.
- FinTech: Financial institutions leverage APIs for secure data exchange between various systems. Robust security measures within the API architecture are crucial for protecting sensitive financial data.
- IoT (Internet of Things): APIs manage data exchange between IoT devices and applications. Scalable architectures ensure efficient handling of large volumes of sensor data, while security measures safeguard device communication.
Latest Tools and Technologies for Building Secure and Scalable APIs
The API development landscape offers a wealth of tools to streamline the creation of secure and scalable architectures:
- API Design Tools: Tools like Swagger and OpenAPI allow for defining and documenting API specifications, promoting collaboration and consistency.
- API Management Platforms: Platforms like Apigee, Kong, and AWS API Gateway provide comprehensive solutions for managing API lifecycles, including versioning, security, and analytics.
- Cloud-Based Infrastructure: Cloud providers like AWS, Azure, and GCP offer scalable infrastructure solutions for hosting your APIs, leveraging elastic scaling capabilities to meet fluctuating demands.
- Containerization Technologies: Containerization tools like Docker enable packaging your API code and dependencies into lightweight containers, facilitating deployment and scaling across different environments.
Read our complete blog on Containerization.
Disadvantages and Trade-Offs
While scalable and secure architectures offer significant benefits, there are also some considerations to keep in mind:
- Increased Complexity: Designing and managing complex architectures can require more upfront effort and skilled personnel.
- Performance Overhead: Security measures like encryption and authentication can add some overhead to API requests, impacting performance.
- Monitoring and Maintenance: Continuously monitoring and maintaining a complex API architecture requires ongoing effort and resources.
Conclusion
Building a scalable and secure API architecture is an investment that pays off in the long run. By adhering to core principles, implementing best practices, and leveraging the latest tools, you can design APIs that can handle growth, adapt to change, and protect sensitive data. Remember, a well-designed API architecture is a cornerstone of a robust and reliable application ecosystem. As API usage continues to explode, mastering these practices will empower you to deliver a secure and performant foundation for your digital initiatives.
Back to Blogs