Security considerations for APIs
Posted by: Prerna | December 02, 2022
Categories: API, API security, Data Validation
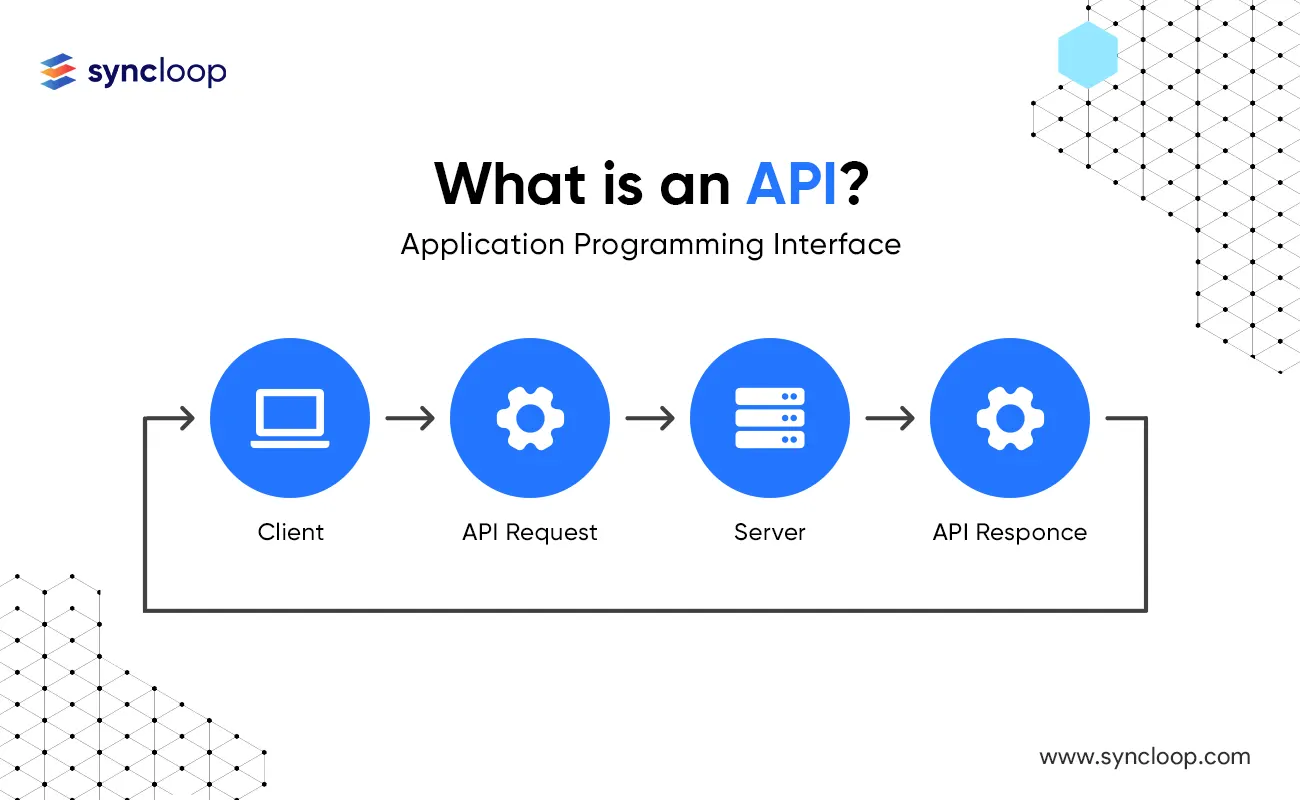
APIs are becoming an increasingly important part of our digital infrastructure, providing access to critical data and services between systems. As we rely more and more on APIs to power our applications, it is imperative that we pay attention to the security of these APIs. With the right security measures in place, APIs can be used safely and securely, and organizations can trust that their data is being handled with the utmost security. In this article, we will explore the essential security considerations for APIs, including authentication and authorization, data validation, and encryption, to ensure that your APIs are secure. With the right security measures in place, organizations can trust that their data is being handled with the utmost security.
Why is API security important?
As we have discussed, APIs are an essential part of modern software architecture. But why is security for APIs important? Building secure software is an essential part of any software development process. Without secure software, organizations risk losing critical information and data, and may even face litigation. When it comes to APIs, security is especially important for two reasons: First, APIs are a gateway to critical data, and if they are not properly secured, this data can be easily compromised. Second, APIs are often used across different systems. If one of these systems has security vulnerabilities or is poorly implemented, it can negatively impact other systems that use that API. Securing APIs, therefore, is critical to ensuring that the data flowing through these APIs is safe and secure.
Essential Security Considerations for APIs
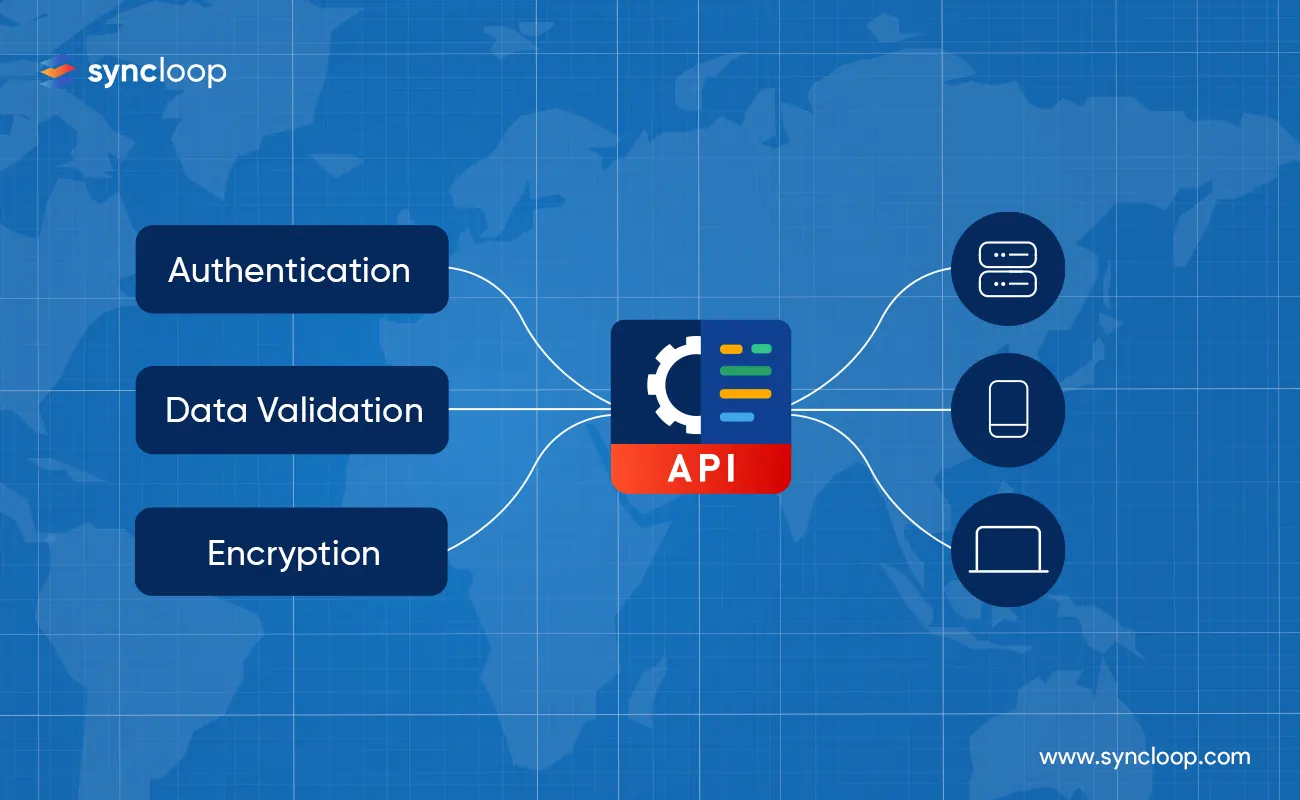
When it comes to security, the most important considerations are authentication, authorization, and data validation. Authentication is the process of ensuring that only authorized users can access the system. Authorization is determining what users are allowed to access and what actions they can perform. Let’s take a look at each of these security considerations in more detail.
Authentication - Authentication is the process of verifying a user’s identity. This can be done through login credentials, tokens, or some other means. Authentication ensures that only authorized users are accessing your system, and that access is restricted to only those who should have it.
Authentication is essential for protecting not only your API, but also the data flowing through it. In addition, authentication can be a critical part of authorization. For example, if a user logs in with a certain set of credentials, they are allowed to access specific data.
Authentication is also critical for ensuring that your API is not being abused or misused. If a malicious user is able to log in to your system and use your API, they can compromise sensitive data and misuse it in harmful ways.
b. Authorization - Authorization, as we discussed above, is determining what users are allowed to access and what actions they can perform. The appropriate level of authorization depends on the context.
In some cases, you may want to allow users to have full access to your API and the data it contains, while in other cases, you may want to limit access to only certain functionality. For example, when creating an API for an internal system, you may want to allow users to access all the functionality, but only within the internal network. If you want to protect your API from other users, you can set a level of authentication, such as a username and password, or a token.
Authentication and authorization are critical for securing your APIs. With these security considerations in place, you can ensure that only authorized users can access your system, and that the data flowing through your API is safe and secure.
Data Validation - Data validation is the process of ensuring that the data that is flowing through your API is accurate and reliable. With data validation, you can scan the data and make sure that it is accurate and safe, including checking information such as email addresses. Data validation can also be helpful when it comes to security. For example, if you are collecting credit card information through your API, data validation can help ensure that the information is accurate and correct.
Data validation can also help you secure your API from certain types of attacks. If a hacker is able to send incorrect information through your API, data validation can help you identify these issues and address them accordingly. Data validation is an important security consideration for your APIs and can help you ensure that the data is accurate and safe.
Encryption - Encryption is the process of converting information into a secret code that is only readable by certain entities or individuals. By encrypting your APIs, you can ensure that the data passing through it is secure, and only those with the key or decryption can access it. Encryption can be used in a variety of ways when securing your APIs. You can encrypt the information when it is in transit, as it is being transmitted between systems, and at rest when it is stored in a database. In addition, you can also encrypt the credentials that are being used to access your API.
Encryption is an essential security consideration for your APIs. If you are transmitting sensitive data, such as credit card information, it is important to ensure that it is being sent in a secure way. By encrypting the data when it is sent, you can protect it from being intercepted. Encryption is a critical security consideration for your APIs and can help you protect your data from being compromised.
Back to Blogs